That is linked to program that makes use of a lookup table to the SubWord move. Observe: This vulnerability only affects products that are no more supported through the maintainer.
Severity: large Exploitation standing: Versa Networks is aware of one particular confirmed consumer reported instance wherever this vulnerability was exploited as the Firewall guidelines which ended up published in 2015 & 2017 weren't applied by that client. This MySQL health check service non-implementation resulted within the undesirable actor having the ability to exploit this vulnerability without the need of using the GUI. within our testing (not exhaustive, as not all numerical versions of key browsers had been tested) the malicious file doesn't get executed to the shopper. there are actually reviews of Other people based on spine telemetry observations of a 3rd party service provider, nevertheless these are unconfirmed up to now.
I might like to supply another Answer for this, which was pointed out in among the list of reviews but not likely described:
The pagination class features arbitrary parameters in back links, bringing about cache poisoning attack vectors.
whether it is, it's going to execute the program that you simply deliver to it. You can also specify for just how long it must check whether the host:port is prepared. As for me This can be the cleanest Option that truly will work.
If mysql service position brings about your application to exited with code one you can use among restart coverage possibilities out there. eg, on-failure
If somebody is familiar with how to get the docker logs mysql inside healthchek It'll be better than permit the question log
I'm striving to be sure that my app container won't operate migrations / start out until the db container is commenced and able to settle for connections.
These parts will probably be investigated extensively depending on the general conduct on the database. Just about every component from the Assessment are going to be specific during the report you’ll obtain next the Health Check.
An issue was learned in Fort prior to one.6.3. A malicious RPKI repository that descends from the (trusted) belief Anchor can serve (by way of rsync or RRDP) a source certification made up of a tiny bit string that does not appropriately decode into a Subject general public vital.
A healthy database could be the backbone of a successful business. By applying MySQL Health Checks, you get a comprehensive idea of your database's performance and prospective concerns, empowering your organization to proactively control your database's health, and making sure a trusted foundation for the applications as well as success of your enterprise.
So I decided to change to a lot more complicated command and use container's exterior ip deal with to be sure that healthcheck is the same as genuine request might be:
This causes it to be feasible for unauthenticated attackers to append more SQL queries into now present queries that can be accustomed to extract delicate data within the database.
At RalanTech, we customize our MySQL consulting services to meet your special wants, collaborating closely to establish remedies that boost your operations and provide optimum worth.
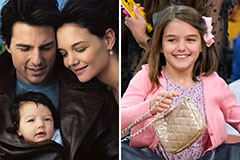 Suri Cruise Then & Now!
Suri Cruise Then & Now! Brooke Shields Then & Now!
Brooke Shields Then & Now! Jane Carrey Then & Now!
Jane Carrey Then & Now! Katey Sagal Then & Now!
Katey Sagal Then & Now! Ryan Phillippe Then & Now!
Ryan Phillippe Then & Now!